Articles |
Entanglement and CryptographyLim Chin Chean
[Editor's note: Quantum cryptography is a active area of research and significant progress has been made since this article was written. Interested readers are recommended to explore the literature for the latest news and updates.]
CryptographyCryptography is an important tool in society as it protects important information from malicious individuals.One of the dominant cryptography schemes would the RSA scheme, which involves mathematical complexities to ensure a secure transfer of information. To have an idea of its security, the fastest computer in the world would take thousand of years to crack the cryptogram. However, the concept of quantum computers poses a threat as any cryptogram could be cracked in matters of seconds.The more secure method would be the one time pad method. With this method, parameters called keys are randomly generated for each character within the intended message. Then, a cryptogram will be produced by the encrypting algorithm with both the key and the message as input. Next, the cryptogram will be sent through public channel, while the keys will be kept private between the sender and the intended recipient. Finally, the same set of key will be used to decrypt the message. As a result, the security of the whole process would rely on whether the keys were sent safely, without interference from any eavesdropper. Since the decryption process requires the set of randomly generated keys, there is no way to break this system mathematically. However, the fact that the distribution of keys involves external (possibly human) factors renders this method vulnerable to man in the middle attacks. Quantum Key DistributionAs stated, the distribution of keys plays a critical role in ensuring the security of a cryptographic system. Amazingly, quantum mechanics has the potential to guarantee the safety of key distribution involved in the one time pad method. In fact, there are quite a few variants proposed by scientists as the ideas of quantum mechanics blossomed in the field of quantum information. Some ideas involve the concept of state 'collapse' in quantum mechanics, while some relied on the idea of entanglement. However, only one protocol will be described in this short article – EPR protocol (Ekert, PRL 1991 (67))EPR ProtocolThis method relies entirely on the idea of entanglement to transfer the keys required in the cryptographic process. This protocol essentially strengthens the security of the one time pad method, where the delivery of keys is based on quantum principles.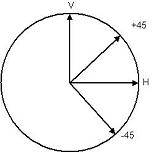 In practice, each member of a pair of maximally entangled photons will be sent to both sender (Alice) and receiver (Bob). As Alice receives the single member of the entangled photons, she would measure the photon's polarization randomly between two pre-determined set of directions – horizontal/vertical (H,V) and +45°/-45° (L,R) – Bob, at his side, will then perform the same steps on his photon. This is where the beauty of entanglement comes in. When a measurement is done on either entangled particles, the other member of the pair will provide a totally opposite / identical (depending on the type of entanglement) result upon measure. For example, a value of horizontal on the first, will give vertical on the second. However, if Bob measures in the LR directions as compared to the HV directions used by Alice, random results will be obtained.
In practice, each member of a pair of maximally entangled photons will be sent to both sender (Alice) and receiver (Bob). As Alice receives the single member of the entangled photons, she would measure the photon's polarization randomly between two pre-determined set of directions – horizontal/vertical (H,V) and +45°/-45° (L,R) – Bob, at his side, will then perform the same steps on his photon. This is where the beauty of entanglement comes in. When a measurement is done on either entangled particles, the other member of the pair will provide a totally opposite / identical (depending on the type of entanglement) result upon measure. For example, a value of horizontal on the first, will give vertical on the second. However, if Bob measures in the LR directions as compared to the HV directions used by Alice, random results will be obtained.
To use the results in communication, we then associate H as 0, V as 1 and similarly L as 0, R as 1. In other words, if Alice and Bob coincidentally used the same set of direction, they will obtain identical (assuming they use a certain entangled state beforehand) values of their results, eg: both 1or both 0. However, if Bob would use a different direction, there is a 0.5 probability of getting the same result. For example, if Alice's value is 0, Bob will either have 0 or 1. In the relevant cryptographic protocol, Alice and Bob will repeat the process multiple times. Then, Alice and Bob will communicate all the directions chosen by them throughout the process in public. Upon comparing their directions, Alice and Bob will separate their results into two groups. The first group will be the values where both parties chose the same set of directions; the second group will be the values where both parties chose different set of directions. The string of values from the first group will thus be the keys used in the one time pad system. Since no physical transfers of keys are involved, this method is inherently secure from conventional system where the transfer must involve a third party. What then would happen when an eavesdropper is present throughout the process? For example, the eavesdropper could intercept some of the photon, measure its polarization and send it out again to Bob. In this case, could the eavesdropper gain any information on the keys after Alice and Bob announced their measured directions in public? Bell's InequalitiesTo detect the presence of eavesdropper, Alice and Bob could use the second group of values to test Bell's Inequalities. If Bell's inequality is violated over a certain accepted degree, the communication could be said to be secure since the photons were still entangled. As the measurement of the eavesdropper would reduce the entanglement between photons, the non-violation (or weak violation) of Bell's inequalities would indicate eavesdropping. Nonetheless, the environment might affect the entanglement of photons during communication, thus Alice and Bob must agree on the range of accepted values before communicating (to compromise the effect).ConclusionUntil now, not much development has been done for this protocol of cryptography due to experimental difficulties surrounding it. Yet, a bank from Vienna had performed a real bank transfer with this protocol on 2004. This thus indicates that such protocol is not mere fictional or unattainable. Despite experimental drawbacks, it is clear that this protocol has the potential to enhance the security of our current cryptographic system. |


